IGEL Blog

Secure Your Edge!
Sadly, in 2021, we’re used to the fact that people are constantly trying to get access to our information. We seem to hear reports from major businesses weekly that some database has been hacked, or supposedly secure credentials have been compromised, and personal details have been leaked all over the internet.
We’ve got to the stage where we no longer labor under the misapprehension that we, or the businesses we use will never be hacked. Instead, we’re into the era of damage limitation. If sensitive information is stolen, the strategy is to make it as difficult as possible to get anything useful from it via encryption, or by keeping key parts of the data separate.
There’s another type of attack though, which is much more insidious. It’s one that doesn’t aim to steal any data. Instead, is about pure blackmail. And it’s on the rise.
Ransomware on the Rise
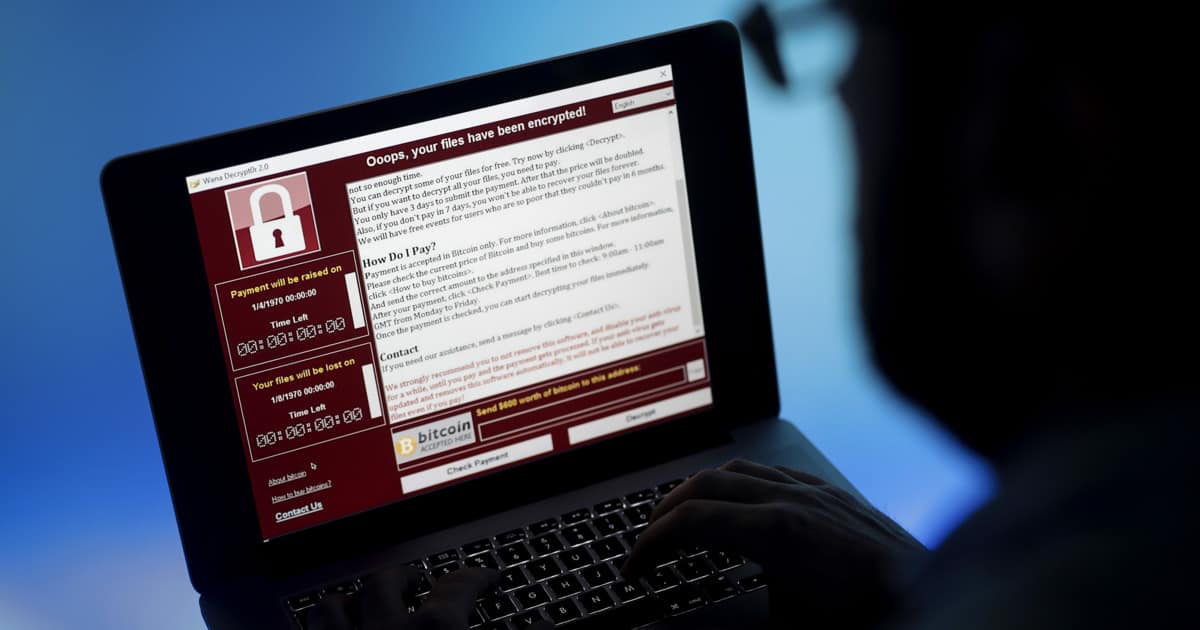
Ransomware has a very simple plan of attack. Make a target’s data unreadable unless the target pays an arbitrary ransom to regain access. This is usually carried out via a ‘worm’ that encrypts the primary Windows system partition and any other partitions discovered. The attacker then demands payment (usually in bitcoin) to release the recovery key. It is only with this key that the infected system’s partitions can be restored and access to the data regained. Without this, the only option is to wipe each affected machine and then reinstall from backups or a fresh installation.
To most people working in IT, the name ‘WannaCry’ brings on a range of different emotions, most of them negative. In 2017, the largest ransomware attack ever to have been carried out hit organizations across the world, leading to billions of dollars of loss and damage.
Shockingly, this attack was carried out via a vulnerability that was not only known about, but that already had an available fix. The exploit used this vulnerability to tunnel into multiple Windows machines on the network, infecting them all in turn. They just had to be running unpatched versions of Windows 7 and earlier.
WannaCry exposed some huge failures in IT security for organizations globally. Approximately 200,000 machines running Windows 7 and earlier were impacted.
Among the hardest-hit victims of this attack was the UK’s National Health Service in England and Scotland. Impacted endpoints included PCs, MRI scanners and equipment in operating theaters. The attack progressed over four days, making vast swathes of critical life-and-death equipment unusable. The total cost to the NHS was £92 million.
Decreasing Presence at the Edge
Windows was and still is a core component for most of the world’s businesses. Attacks like this, though, highlight that having a large, complex operating system across multiple sites, networks and geographies can lead to a huge attack surface, no matter what mitigations are in place. There is only so much you can diminish against malicious actors, employees and network connections.
Increasingly, organizations are looking at ways to decrease their presence at the edge. With the rise in SaaS applications, VDI implementations that put Windows securely in the datacenter and the Digital Workspace, it has become less important to have a traditional operating system everywhere that application access is required.
Moving Windows to the datacenter is something that forward-thinking organizations have been doing for over 20 years. VDI keeps Windows locked in the datacenter, with all of the additional security that incorporates, including industrial firewalls, monitoring and easy update methods.
IGEL: The Operating System Purpose-Built for the Edge
The edge is increasingly becoming the preserve of purpose-built ‘edge’ operating systems, such as IGEL OS. These operating systems prize security, connectivity and application access above all else. By acting as truly stateless devices, nothing sensitive is stored locally, with everything taking place in the public and private cloud as required, with all of the additional security mentioned above.
Rather than managing herds of temperamental large operating systems which are all built slightly differently depending on the use case across departments, geographies and use cases, IGEL OS enables all endpoints to be managed as a consistent fleet, with integrations into third party tools as required.
Here’s an example of how IGEL can help:
Imagine for a second that despite all of your best efforts and security solutions, a swathe of your Windows endpoints have fallen victim to a ransomware attack and are now encrypted. How do you cope with that situation? Can you now trust your endpoints? How do you get your users productive on endpoints they can’t currently use?
This is where IGEL’s UD Pocket solution comes in. With a UD Pocket, users can get up and running with their SaaS and VDI environment on the same device they were using previously, but without using the compromised OS that’s installed on the hard drive. That’s the benefit of running a secure, containerized operating system; it abstracts from the endpoint but enables full access to all of the applications and services users need.
Wanna avoid the next WannaCry? Secure your edge.